
ADB Pull Data Extraction from Android Devices: Explanation & Process - Video & Lesson Transcript | Study.com

ADB Hoist Rings - Center Pull Hoist Ring: Screw-On, 5,000 lb Working Load Limit - 06921332 - MSC Industrial Supply
GitHub - zzz40500/ADB-Duang: Plugin for one key pull file ( database,preference ) from device and push file( database,preference ) to device

adb - I am trying to pull the app data from my phone to my pc but it says the path does not exist? - Android Enthusiasts Stack Exchange

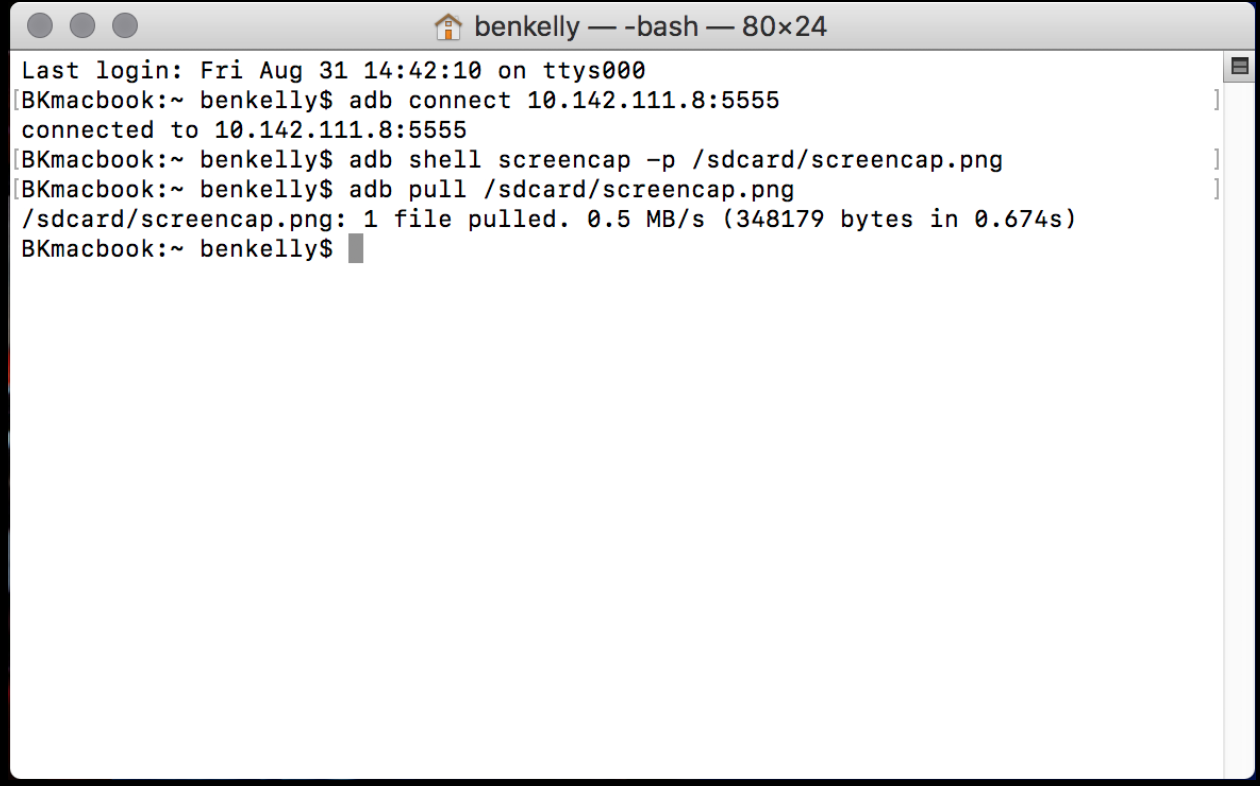





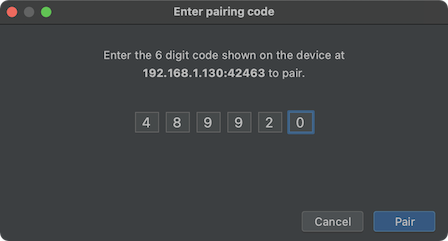

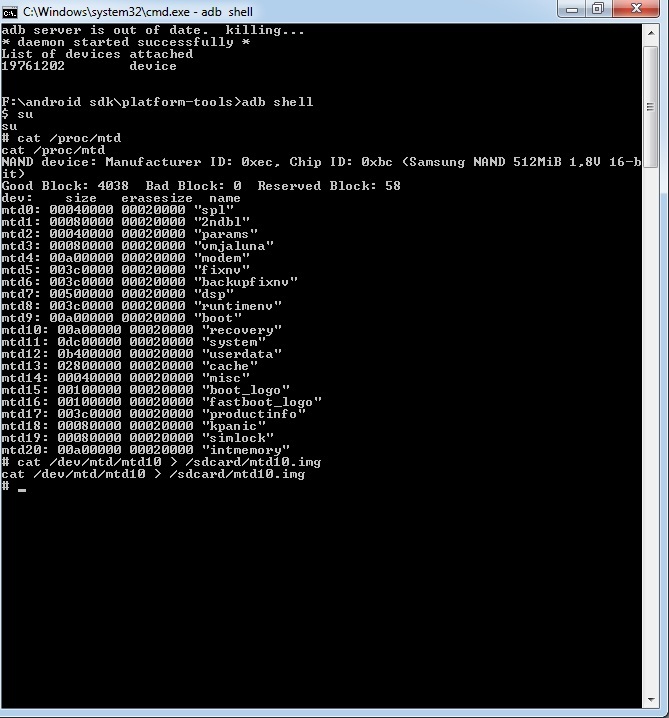

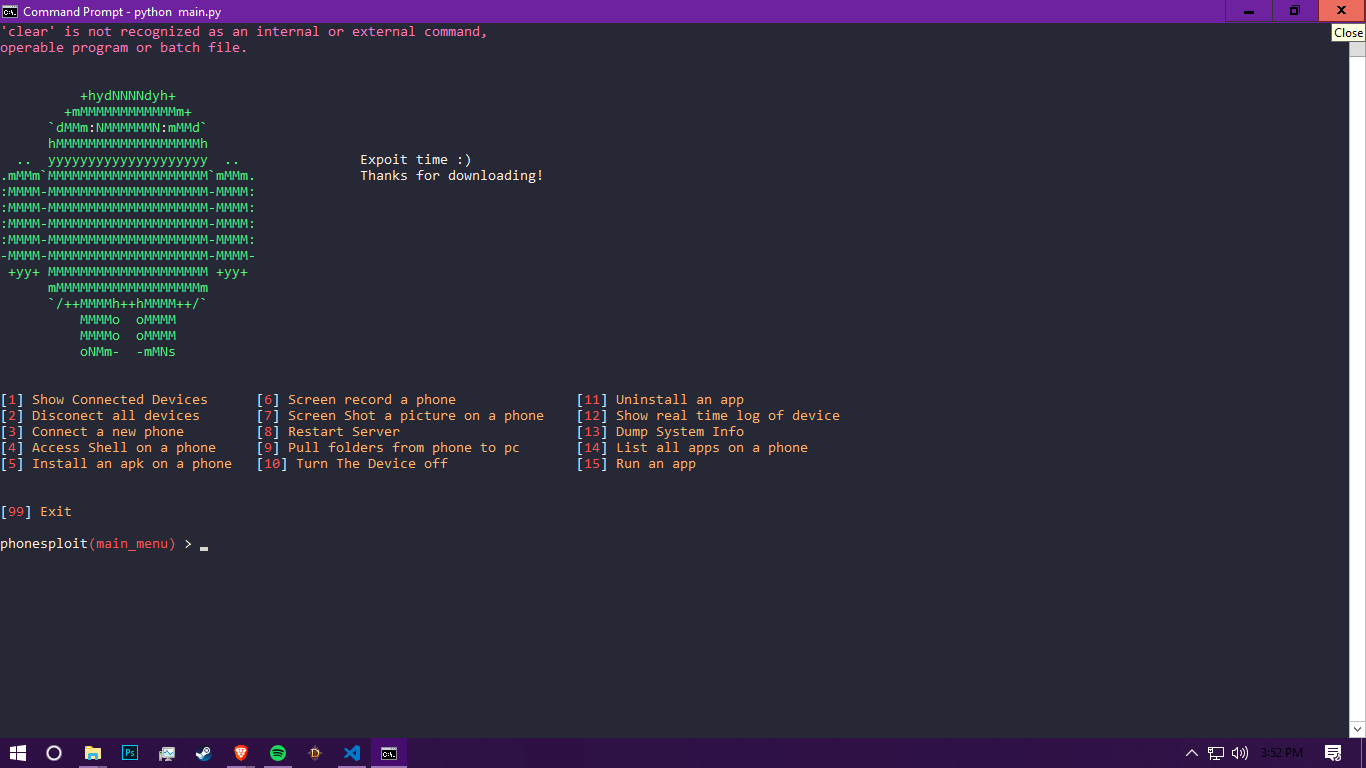






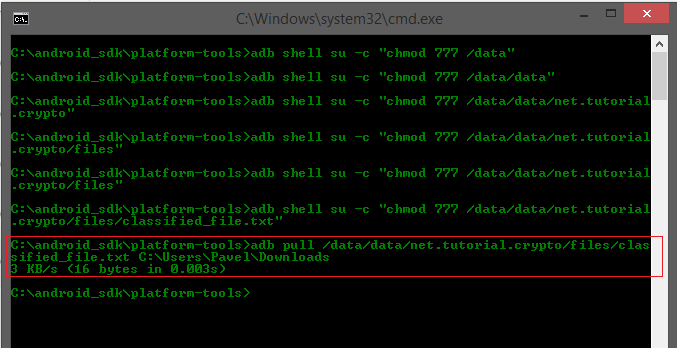
![How to transfer files using ADB push and pull commands [2023] How to transfer files using ADB push and pull commands [2023]](https://cdn.compsmag.com/wp-content/uploads/2022/02/How-to-transfer-files-using-ADB-push-and-pull-commands.jpg)
